Do NOT follow this link or you will be banned from the site!
National Registry Of WI-FI Connections
Submitted by thedosmann on Tue, 06/20/2017 - 15:18
 There are many cyber threats that we face in today's ever evolving internet. One of those threats, that has not received a lot of attention, is the growing number of Wi-Fi hotspots that millions of cell phones connect to daily.
There are many cyber threats that we face in today's ever evolving internet. One of those threats, that has not received a lot of attention, is the growing number of Wi-Fi hotspots that millions of cell phones connect to daily.
Along with the obvious threat of compromising private data and passwords, there are other security threats which can be easily imagined with smartphones connecting to unsecured hotspots. Some of the known attacks and methods used by hackers are phishing, man-in-the-middle, Trojans, worms, and unpatched software, to name a few. This doesn't account for other smartphone vulnerabilities like Bluetooth attacks.
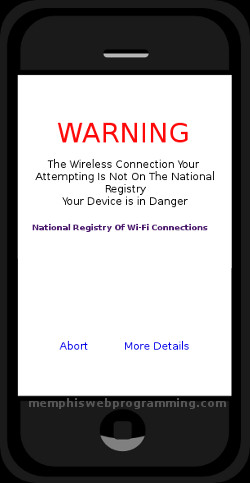
The unsecured Wi-Fi connection problem is an evolving one that we could get a grip on before it grows to the extent that it is uncontrollable. One way of doing this would be a National registry of Wi-Fi hotspots that would keep track of the Wi-Fi connections around the nation. Cell Phone providers could easily incorporate a process in their phones that would check the registry when a user is connecting to a hotspot. If the Wi-Fi hotspot is not listed the user will be warned that the internet connection is not safe because the hotspot is not on the registry and that their phone is in danger if they connect. The registry listing check could be streamlined by using GeoIP, so that only the Wi-Fi connections with-in a certain range of the cell phone is checked.
To illustrate how unsecured Wi-Fi connections could be not only be a threat to the individual user but potentially a National threat, I offer the following scenario.
A motivated hacker could set up a network of a few command servers hidden behind spoofed IPs that are controlled by a central command and control server. He could then place free Wi-Fi hotspots up, strategically placed to capture the most cell phone connections possible. On the connection, the Wi-Fi server auto loads a landing page which directs the user to 'click here' to continue to the internet. That click infects the cell phone with a carefully scripted virus that lays dormant awaiting instructions. Before going dormant, it emails a link to all of the phone's contacts. The link is to a web page that is crafted to get the visitor to infect his device with the same virus. The following is one of many possible scenarios which uses extremely conservative numbers.
100 Wi-Fi hotspots are set up across the top 10 largest cities in the U.S., which includes over 25 million people(2.5 million per city). While this may seem a large number keep in mind you can have multible Wi-Fi spots strategically placed across a major city and the connections would not be simultaneous.
In this population, if the hacker is able to get just 1% to connect to the Roque hotspots, that is 250,000 infected cell phones. On average there are 25 contacts per phone; that is 6,250,000. The hacker is able to get just 1% to connect with the link sent in the email; that is 62,500 additional recruits. The hacker now has control of over 300,000 cell phones in just 1 itineration of the recruitment process. The hacker continues the email recruitment process another 5 times, using the additional contacts from each new recruit(5x62,500), and using the above percentages he has over 600,000 cell phones at his command.
Because they are running up against the time constraints of being detected they go forward at this time with te botnet and issue the command from the command and control server, which in turn reverberates throughout the command server network and finally to the cell phone army of recruits. This scenario will fall short of outlining an actual target or purpose but let your imagination take over from here; What could you do with 600,000 smartphones at your command?
A National registry of Wi-Fi connections along with cell phone provider software could limit the potential for this type of security threat. Clearly, the setup, procedures, and processes, of this type of registry would require significant infrastructure, but these are the types of steps we need to make in order to stay ahead in cyber security.
by Jim Atkins
Share it now!