Do NOT follow this link or you will be banned from the site!
Geo-targeted IP and DDoS
Submitted by thedosmann on Mon, 06/09/2014 - 11:10
Geo-targeting
Geo-targeting an IP address is a simple process that includes obtaining the IP address of an incoming connection and running a quick code check that returns where the IP originated geographically. This technique is widely used for targeted ADs, server traffic analysis, content presentation, and other geographic based information gathering. The process becomes complicated when dealing with spoofed IP addresses. A spoofed IP is one that does not contain accurate IP address information. While it is possible to spoof an IP, there are tools that can look deeper and determine the true source of an IP packet that include Network Ingress/Regress Filtering, Reverse Path Forwarding, reverse tunnels for mobile connections, and other methods.
Visualization of Internet map
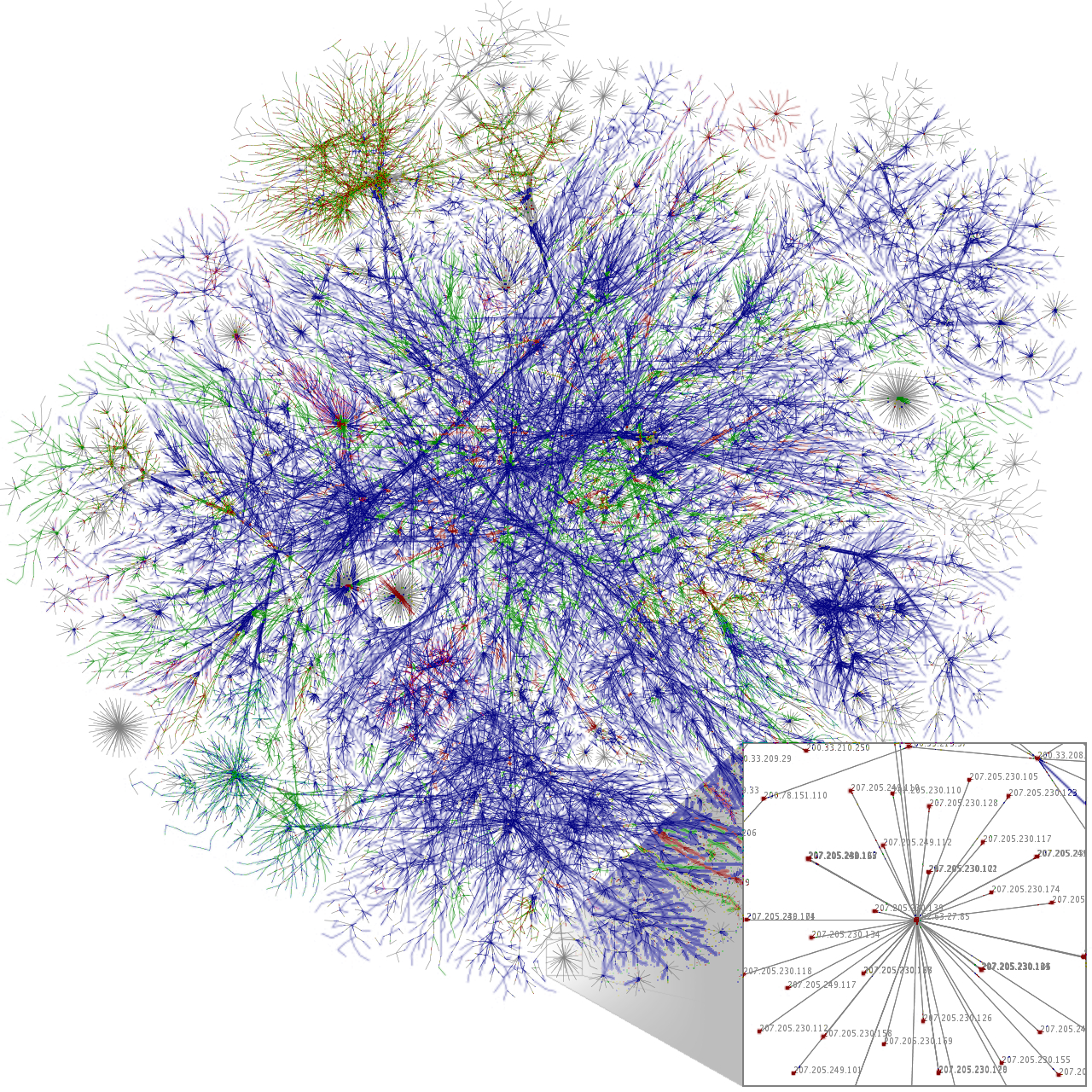
Along with geo-targeting an IP, it is also possible to trace what route the particular packet has taken to arrive at the server. Back-tracking the path an internet packet took allows for discovery of the geographic location of the major internet communication backbones the packet traveled. Along these routes there are network operations centers that can be identified and accessed via their IP address. If filtering is engaged then the true route can be determined by tracing the IP route to the source IP and if a valid route is established then a proper response can be formulated. In some cases this might require a chain of back-traces that follow a number of invalid IPs or even malformed packets.
DDoS
During a DDoS attack a server might be attacked by hundreds or thousands of different IP addresses. In the past the main line of defense was blocking, rerouting, and redistributing, these IPs using a variety of methods. The problem with this approach is that the sheer number of attackers will quickly degrade server resources, leaving it vulnerable. Additionally, DDoS attackers have morphed their approach over the years that make it more difficult to recognize and combat their activity. A vital consideration is the server overhead required to first determine if an attack is ongoing and then formulate a response to the attack. The more assets you build into server resources only causes an escalation in the attacks and numbers used.
The current approach of stand your ground is not working in the fight for server defenses. If we look back at past battles and wars we can understand how just building better defenses is not enough. If the enemy has the determination and ability to escalate its resources it won't be long before your defenses are not enough. As you build up your defense the enemy will continue to find ways to circumvent and prevail.
Recognizing there is a problem
One of the major issues that need to be worked out is an efficient attack recognition system allowing for automated responses. If we look back at some of the recent internet attacks a glaring constant stares back, either the recognition that there was an attack was too late or not there at all. This means that a defense preparation and response strategy must first and foremost be able to accurately and quickly detect that an attack is imminent or already in progress. Once a stable and persistent recognition system is in place a geo-targeted approach to defending server assets can implemented.
This would involve off-network nodes geographically placed around the nation's communication infrastructure capable of accepting intelligence from a watchdog server on the server network and programmed to act upon that intelligence. Responses and actions could include ISP and domain notification of an ongoing spoofed IP packet flow and back-tracing these through the network of routers and exchanges the spoofed packets are following.
Distributed Defense
The initial call to action would be triggered by a watchdog system that would determine an attack is in progress. The watchdog system would hand this information off to an off-premise central messaging node and in turn the messaging system would notify the nodes nearest the geo-locations of the attacking computer routes. Additionally, the watchdog system at the location being attacked will update the off-premise messaging server of changes so it can update the various nodes being used to trace the attack and incorporate other nodes as needed. Subsequently, the off-premise nodes would report back with IP and routing intelligence. This type of defense takes the fight closer to the attacking computers and removes the resource intensive fight from the server being attacked and the bandwidth it uses.
Along with the benefits of a distributed defense there are the benefits of historical intelligence across the nation's communication backbones. IP addresses and routes may change but through historical reference some constants will develop. There is also the possibility of shared defenses across the massive number of communication routes that traverse our nation. Just as there are peering and transit agreements there can also be shared defense agreements.
A national infrastructure like this would also expose ISPs and routes that allow non-network IPs to originate from their network.
by Jim Atkins
Share it now!